MyLittlePwny - JustCTF
A simple “PWNING” challenge, that I found to be more of a bash challenge. Requires you to discover the correct escape character in order to execute bash commands, some of which are filtered. As such, you must find the command that can output the flag that has not been restricted by the program itself. While simple, it was a fun challenge and a great way to get my feet wet again coming back from my little sabbatical.
Analysis
Connecting the given server using the command provided nc mylittlepwny.nc.jctf.pro 1337, we are greeted with a “terminal” that echoes our input back to us with a new ascii art each time.

Trying different format string specifiers like %x or %p did not return anything interesting except a message from program that states I can't swear ;(. With this message we filter through special characters to see which are blacklisted and which are allowed through trial and error.
The results showed that with the backquote (`) character we get a new error message directly from a bash shell.
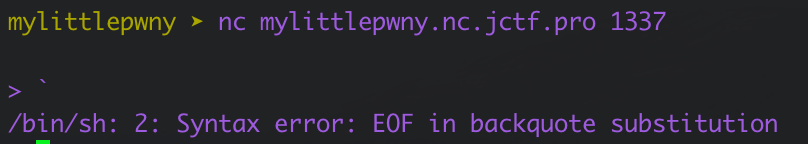
Looking this up we know this error occurs when you run bash commands using the backticks and do not properly pair (ie. close) them. Testing this out we can attempt a code injection using `<cmd>`. When executed in the service’s terminal we can see that we are indeed succesful with the command injection.

With the ls command we see the flag is in the same directory as the running program (assuming its the server.py program we also see). Trying to cat the flag out doesn’t work as the program has prepared responses for this command as shown:

Trying other commands such as less or more won’t work as they are filtered as well.

From before we know we can’t use pipes or stream redirects (<flag) as those are blacklisted by the program. Fortunately there is one command that wasn’t caught and outputs properly to the echoed portion of the program. This being the base64 command. With this we can run it against the flag file to extract its contents in the form of a base64 encoded string.

From here we simply copy and paste it into our own terminal and decode with echo <flag> | base64 -d to retrieve the flag.
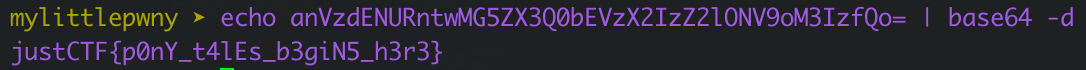
justCTF{p0nY_t4lEs_b3giN5_h3r3}
